Mobile App Security: Revealing Vulnerabilities for Enhanced Protection
Your teams develop mobile apps and you’ve already implemented all the security best practices, yet you want even more peace of mind? This blog is for you.
Recently, I’ve been learning about reverse engineering Android apps and exploring how attackers see your app and uncover vulnerabilities. This hands-on experience led me to search for a tool that could automate the process.
So, how do you reverse engineer Android apps?
- Download the APK: Obtain the APK file of the app you want to analyze.
- Extract the APK files: Unzip the APK file and locate the DEX files. A DEX file contains compiled code for the Android platform.
- Convert DEX to JAR: Use the ‘dex2jar’ open-source tool to convert the classes.dex file to a JAR file.
What can you discover through this process?
- Unobfuscated Code: View the app’s code in a readable format.
- Leakage of Sensitive Data: Identify hardcoded values, secrets, or sensitive data.
- APIs Being Used: Discover the APIs the app interacts with.
Looking to automate this process?
MobSF (Mobile Security Framework) is your answer. It’s an open-source, automated mobile application security testing tool that conducts static and dynamic analysis of Android and iOS apps.
MobSF
MobSF integrates several open-source projects and tools like Androguard, MobSF API, iNalyzer, and more.
Features of MobSF:
- Automated Security Scanning: Identifies vulnerabilities, including sensitive data disclosure, insecure cryptography, and insecure communication.
- Dynamic Analysis: Analyzes runtime behavior, code injection, and traffic interception.
- Static Analysis: Analyzes source code, binary, and configuration.
- Reverse Engineering: Provides de-compilation, disassembly, and debugging capabilities.
- Integration with CI/CD: Supports integration with CI/CD pipelines to ensure app security throughout the development lifecycle.
Examples of tasks executed by MobSF based on logs:
- Perform Static Analysis of Android APK
- Generate Hashes
- Unzip APK
- Extract AndroidManifest.xml
- Convert AXML to XML
- Parse AndroidManifest.xml
- Fetch Icon Path
- Extract Manifest Data
- Fetch Details from Play Store
- Analyze Binary
- Read Code Signing Certificate
- Run APKiD 2.1.5
- Decompilation and Code Analysis
- Decompile to Java
- Convert Java to Smali
- Start Code Analysis
- Additional Analysis
- Run NIAP Analyzer
- Finish Code Analysis and Extract Email/URL
- Extract Data from APK and Source Code
- Detect Firebase URLs
- Perform Malware Check on Extracted Domains
- Additional Actions
- List Source Files
- View Java Source Files
Getting Started:
The easiest way to start is by using the Docker container, which can be set up in just a few minutes. You can get started with only the 2 commands below:
docker pull opensecurity/mobile-security-framework-mobsf
docker run -it --rm -p 8000:8000 opensecurity/mobile-security-framework-mobsf:latestThen open the portal by going to http://localhost:8000
Upload the build and wait for it to scan. In the screenshots below, I have uploaded a sample android app for demo purposes.
Below is what I could find within minutes:
- Application is signed with a debug certificate
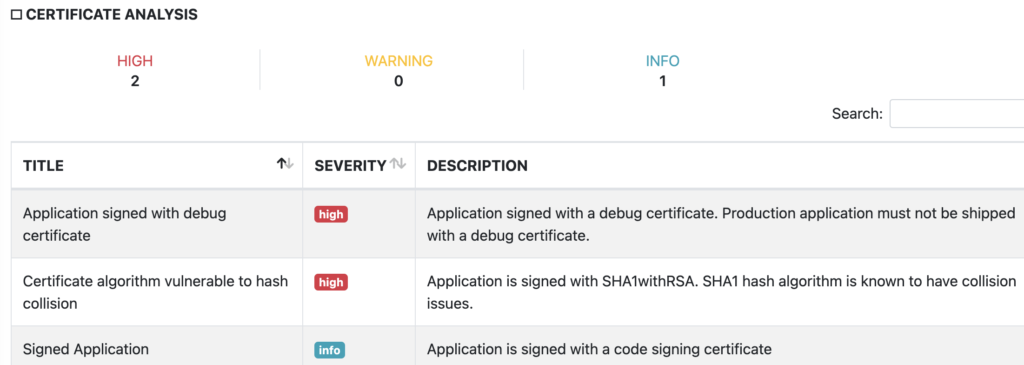
- App is compiled in debug mode

- App is using weak encryption
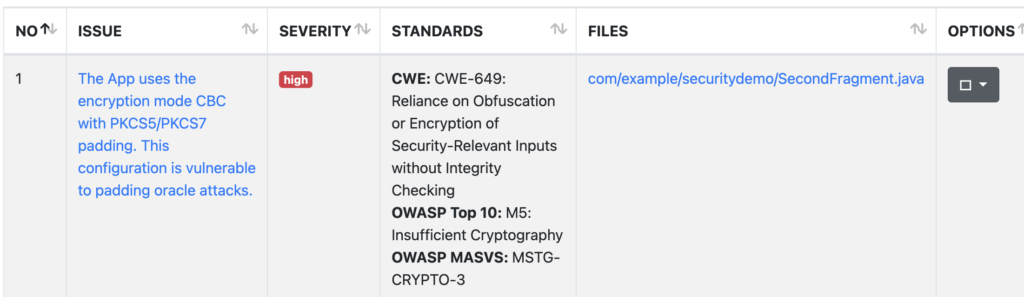
- View java source code

Key benefits of the tool:
They key benefit here is to be able to put this tool post all security mechanism (code obfuscation, multiple scanning tools, best practices, code review, static code analysis..) and have a check from the attacker’s eye before uploading your builds. In this case, at no additional cost, rapidly and automatically, you can detect:
- Leakage of secrets
- Weak encryption
- Un-obfuscated code
- App is in debug more
- And many more..

